Israel stunned and hobbled Iran starting on June 13, 2025 when it pulled off an intelligence and military operation years in the making that struck high-level targets with precision. Guided by spies and artificial intelligence, the Israeli military unleashed a nighttime fusillade of warplanes and armed drones smuggled into Iran to quickly incapacitate many of its air defenses and missile systems. With greater freedom to fly over Iran, Israel bombarded key nuclear sites and killed top generals and scientists. By the time Iran mustered a response hours later, its ability to retaliate — already weakened by past Israeli strikes — was greatly diminished.
The Mossad and the military worked together for at least three years to lay the operational groundwork…To further diminish Iranian air defenses and missile systems, Mossad agents had smuggled precision weapons into Iran that were prepositioned to strike from close range…Those weapons included small, armed drones, which agents snuck into the country in vehicles…Mossad agents stationed weapons close to Iranian surface-to-air missile sites…To analyze information gathered from various sources, Israel used the latest artificial-intelligence…AI was used to help Israelis quickly sift through troves of data they had obtained….An investigation by The Associated Press conducted in early 2025 uncovered that the Israeli military uses U.S.-made AI models in war to sift through intelligence and intercept communications to learn the movements of its enemies. It’s been used in the wars with Hamas in Gaza and with Hezbollah in Lebanon.
In addition to AI, the Mossad relied on spies to identify top nuclear scientists and members of Iran’s Revolutionary Guard… At least eight members of the Guard, including the head of its missile program, were killed in a single Israeli strike on an underground bunker.
Another facet of the attack was to strike Iranian vehicles used to transport and launch missiles. The strategy was similar to a Ukrainian operation earlier this month in Russia. In that operation, nearly a third of Moscow’s strategic bomber fleet was destroyed or damaged with cheaply made drones snuck into Russian territory…In an interview with Iranian state-run television, the country’s police chief, Gen. Ahmadreza Radan, said “several vehicles carrying mini-drones and some tactical drones have been discovered.” ….
In the 2000s, Iranian centrifuges used for enriching uranium were destroyed by the so-called Stuxnet computer virus, believed to be an Israeli and American creation….In 2018, Israel stole an archive of Iranian nuclear research that included tens of thousands of pages of records…In July 2024, Israel killed a senior leader of Hamas, Ismail Haniyeh, with a bomb in a bedroom of a government guesthouse in Tehran.
Excerpts from JULIA FRANKEL and SAM MEDNICK, How Israel used spies, smuggled drones and AI to stun and hobble Iran, AP, June 17, 2025








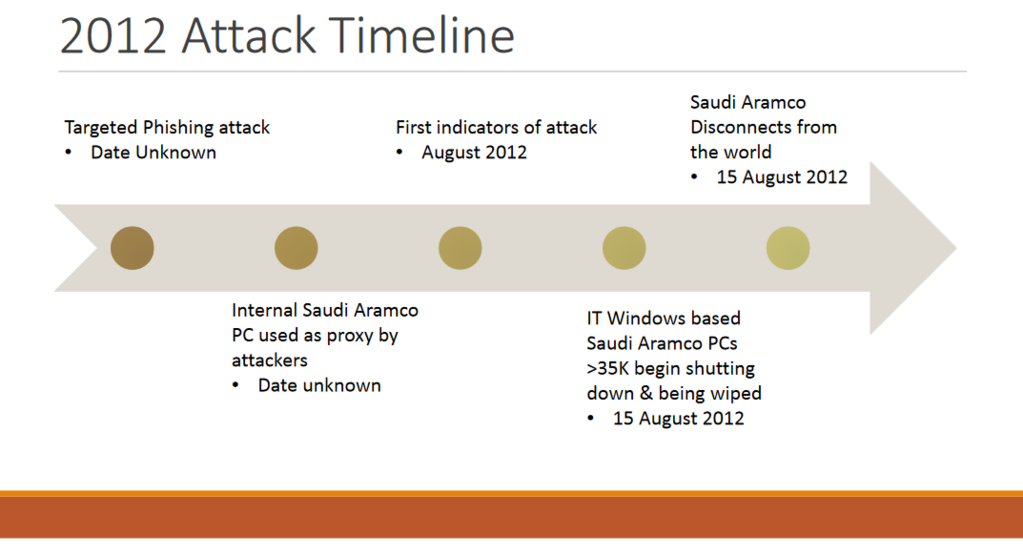

 On June 22nd 2017,
On June 22nd 2017, 