[When governments buy weapons] it is standard to supplement the main deal with a side contract, usually undisclosed, that outlines additional investments that the winning bidder must make in local projects or else pay a penalty. Welcome to the murky world of “offsets”.
The practice came of age in the 1950s, when Dwight Eisenhower forced West Germany to buy American-made defence gear to compensate for the costs of stationing troops in Europe. Since then it has grown steadily and is now accepted practice in 120 countries. It has its own industry newsletter and feeds a lively conference circuit. The latest jamboree, hosted by the Global Offset and Countertrade Association, was held in Florida…. Yet its very structure serves to mask a build-up in the unrecognised financial liabilities of companies. It also, critics argue, fosters corruption, especially in poorer parts of the world.
Avascent, a consultancy, reckons that defence and aerospace contractors’ accrued offset “obligations”—investments they have promised but not yet made—are about $250 billion today and could be almost $450 billion by 2016. The industry’s own estimates are lower, but all agree the trajectory is upward.
Offsets come in two types. Direct offsets require investment in or partnerships with local defence firms. The idea is to develop self-sufficiency. Turkey, for instance, now meets half its own defence needs thanks to such arrangements. Indirect (non-defence) offsets include everything from backing new technologies or business parks to building hotels, donating to universities and even supporting condom-makers. Here the stated intention is to achieve more general economic or social goals.
Both types of offset are controversial. Economists view offsets as market-distorting. The World Trade Organisation bans their use as a criterion for contract evaluation in all industries except defence. Anti-corruption groups see them as a clever way to channel bribes. Even if many offset deals are clean, they are widely seen as a “dark art”, admits an industry executive. “Offset” has become a dirty word; the industry now prefers the euphemistic “industrial participation”.
The practice is frowned upon in some advanced economies. The European Commission is trying to impose a ban on all offsets in EU-to-EU contracts, and on indirect offsets when the supplier is from outside the union…
America has long been officially against offsets, though it practises something similar at home under the Buy American Act of 1933, which requires foreign arms-makers to source much of the work locally… And as embassy cables published by WikiLeaks make clear, America’s diplomats are sometimes closely involved in its firms’ discussions with foreign governments, including even squeaky-clean Norway’s, over proposed offsets.
In less developed countries, where defence spending is generally rising, offsets are booming. One appeal is that they can be recorded as foreign direct investment, boosting the government’s economic-management credentials. The two biggest arms-buyers in the Gulf, Saudi Arabia and the United Arab Emirates, have long-standing, sophisticated offset programs…Brazil and India are catching up…
This growth is fuelling a thriving offsets industry. At one end are dozens of small brokers who hawk ideas for offset projects to arms-makers and their clients. With the right contacts in government and the armed forces, even small outfits can service the largest defence firms. Take Dolin International Trade & Capital, a one-man operation run by Dov Hyman from his home in suburban New York. Mr Hyman cut his teeth as a textile trader in Nigeria. Today he advises African governments looking to use offsets while helping multinationals craft offset packages.
Further up the chain are a few sophisticated outfits that structure complex deals and arrange financing. The best known is London-based Blenheim Capital. These are assembling ever more creative packages, including, for instance, helping procuring countries to use contractors’ offset obligations as collateral for loans, backed by the “performance bonds” that firms set aside to cover unfulfilled obligations.
These middlemen are offsets’ most vocal defenders. Mr Hyman cites reams of examples of deals that he believes brought great benefits for purchasing countries’ economies. The best of them are “beautiful solutions”: for instance when arms-sellers satisfy offset obligations by guaranteeing credit lines for local manufacturers, thus reducing their financing costs. Using a multinational’s good standing in this way is “an efficient means of making possible transactions that otherwise wouldn’t be viable,” he argues.
However, some projects take contractors disconcertingly far away from their core competence. Take the shrimp farm set up in Saudi Arabia in 2006 with backing from Raytheon, a maker of radar systems and missiles. Praised at first as a model offset, it reportedly struggled to keep its pools properly maintained in searing temperatures and eventually went bust.
Moreover, the academic literature on offsets suggests that the promised benefits are elusive. There are some technology-transfer success stories: for instance, China has boosted its defence-manufacturing capability by requiring offsets when buying kit from Russia. However, research by Paul Dunne of Bristol Business School and Jurgen Brauer of Augusta State University has found that such deals are generally pricier than “off-the-shelf” arms purchases and create little new or sustainable employment. The offsets associated with the giant South African arms purchases of the late 1990s have created 28,000 direct jobs, claims the country’s government. Even if true, it is well below the 65,000 first envisaged. India’s auditor-general recently concluded that some offsets have produced no value for the country.
Judging performance is hard because of a lack of openness. Asked for confirmation of the fate of the shrimp farm, the Saudi offset authority said it kept “minimum information” on projects after their founding and suggested contacting its commercial backers. Raytheon declined to comment and suggested contacting the Saudis. DevCorp, another backer, did not respond. A study published in February by Transparency International, an anti-graft group, found that a third of governments that use offsets neither audit them nor impose due-diligence requirements on contractors.
Worse, accounting rulemakers have failed to impose any requirement to disclose offset liabilities. Companies can thus choose how, or whether, to put them on the balance-sheet. Defence firms have lobbied successfully for offsets to remain classified as “proprietary”, so they do not have to disclose their obligations. In some ways things have got worse: the Commerce Department’s annual report on American contractors’ offsets no longer even breaks out the numbers country-by-country.
This murkiness makes it hard to determine who really pays for offsets. On the face of it, the defence companies do. But Shana Marshall, an offsets-watcher at George Washington University, believes that they build the cost into their bids. Politicians and officials in procuring countries know that they are paying the bill through padded prices, but they accept this because offsets give them some grand projects to trumpet and sometimes provide palm-greasing opportunities.
A study in Belgium found that the country ended up paying 20-30% more for military gear when offsets were factored in. If the costs are largely borne by taxpayers, the benefits accrue to individuals and institutions chosen by the procuring government. This make offsets a good way to conceal delivery of public subsidies to interest groups, according to Ms Marshall.
A number of deals have been exposed as, or are suspected of being, corrupt. A commission has been set up to look into South African contracts dating back to 1999; the government has already conceded that offset credits changed hands at inflated prices. Since 2006 prosecutors in Portugal have been investigating offsets connected with a €1 billion ($1.3 billion) submarine contract with Germany’s Ferrostaal, HDW and ThyssenKrupp. Three Ferrostaal board members and seven Portuguese businessmen are on trial, charged with fraud and falsifying documents. EADS, a large European contractor, is facing multiple inquiries over its sale of 15 Eurofighter planes to Austria. Prosecutors in Vienna and Munich are looking into allegations that millions of euros in kickbacks flowed through a web of offshore firms and side-deals, linked to offset agreements worth €3.5 billion, twice the value of the main contract. (In other words, EADS was supposed to generate €2 of business for Austrian firms for every euro it received for the planes—an unusually high ratio even in fiercely bid contracts.) Tom Enders, EADS’s chief executive, told Der Spiegel, a German magazine, that he “knew nothing about the shadowy world of dubious firms allegedly behind this.” The company says it is co-operating fully with prosecutors and that an internal investigation has so far found no evidence of punishable activity.
Prosecutors are also looking into whether AgustaWestland, part of Finmeccanica, an Italian defence firm, paid bribes to secure the sale of 12 helicopters to India in 2010. Finmeccanica’s former chief executive and the former head of AgustaWestland are due to go on trial next month. According to Italian court filings, suspicious payments allegedly flowed through a sham offset contract for software with help from a Swiss-based consultant. The helicopter-maker and the charged individuals deny wrongdoing.
Industry figures point out that all but the Indian case are at least five years old. They argue that corruption is harder to get away with today because of stricter anti-bribery laws and enforcement in America and Europe. Companies’ general counsels pay much more attention to offsets than they did a decade ago, says Grant Rogan, the head of Blenheim Capital.
Even if graft really is on the wane, offsets’ complexities make it hard to measure the true cost of defence deals. Procuring governments may apply generous “multipliers” to give extra credit to projects they deem exceptionally beneficial, especially if they are keen to buy the kit in question. As a result, defence contractors often find their liabilities turn out to be a lot less than their nominal obligations. A $5 billion sale of military kit might come with, say, $4 billion of gross offset requirements, but after multipliers it might only cost $500m to fulfil. A book on the arms trade, “The Shadow World”, by Andrew Feinstein, describes a contract Saab won in South Africa: to receive more than $200m in credits all the planemaker was required to do, the book says, was to spend $3m upgrading pools in Port Elizabeth and marketing the town to Swedish tourists. Saab says the tourism project cost much more, and suggested that it was up to the authorities to decide what value they put on what it achieved.
This sleight-of-hand helps to explain why industry executives are better disposed towards offsets in private than in public, says Ms Marshall. They say they could happily live without them, but they do not lobby to have them banned. Indeed, some big contractors see their ability to craft a package of attractive offsets as a “source of competitive advantage”, as Boeing’s boss, Jim McNerney, puts it.
The largest such firms will employ dozens of offset specialists to give them an edge in bidding. Lockheed, another American contractor, has about 40. As long ago as 2005 the firm was touting its leadership in offsets to win Thai contracts, according to a leaked diplomatic cable. A downside for the companies is that dealing with national offset agencies can be frustrating. And though the companies’ offset liabilities are smaller in reality than on paper, they can still be daunting: one American contractor, for instance, has $10 billion of nominal obligations in a single Gulf state that will cost $1 billion-2 billion to fulfil, according to a consultant (who will not say which firm or country)….
How long can the offsets boom last? But in the shorter term, their growth will be fuelled by American and European contractors’ intensifying efforts to sell outside their shrinking home markets, to big developing countries whose defence budgets are growing…. Remarkably, offsets are now said to be the main criterion in contract evaluation in Turkey and some Asian countries—more important than the price or the technical capability of the defence equipment itself.
The defence industry: Guns and sugar, Economist,May 25, 2013, at 63
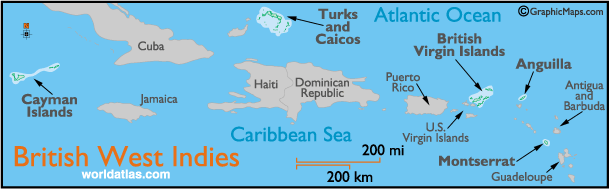 Britain ended its slave trade in 1807, and freed the slaves in its Caribbean colonies by 1838. The British government borrowed £20m, then around 40% of the budget, to meet 47,000 claims for loss of human property. The former slaves got nothing.Close to two centuries on, Caribbean politicians want redress. The Caribbean Community (Caricom) which links former British colonies with Suriname and Haiti, established an official reparations commission in July 2013 and has approached a British legal firm, Leigh Day, for advice…Among the precedents for financial reparations, West Germany and Israel signed a financial agreement in 1952, seven years on from Auschwitz. In June this year, after legal action by Leigh Day, Britain conceded payments averaging £2,600 ($4,000) each for 5,228 now elderly Kenyans who were brutally mistreated during the suppression of the Mau Mau rebellion in the 1950s. Britain’s courts will not now consider claims for atrocities occurring before 1954. Unpicking wrongs from 60 years ago is hard enough.
Britain ended its slave trade in 1807, and freed the slaves in its Caribbean colonies by 1838. The British government borrowed £20m, then around 40% of the budget, to meet 47,000 claims for loss of human property. The former slaves got nothing.Close to two centuries on, Caribbean politicians want redress. The Caribbean Community (Caricom) which links former British colonies with Suriname and Haiti, established an official reparations commission in July 2013 and has approached a British legal firm, Leigh Day, for advice…Among the precedents for financial reparations, West Germany and Israel signed a financial agreement in 1952, seven years on from Auschwitz. In June this year, after legal action by Leigh Day, Britain conceded payments averaging £2,600 ($4,000) each for 5,228 now elderly Kenyans who were brutally mistreated during the suppression of the Mau Mau rebellion in the 1950s. Britain’s courts will not now consider claims for atrocities occurring before 1954. Unpicking wrongs from 60 years ago is hard enough.