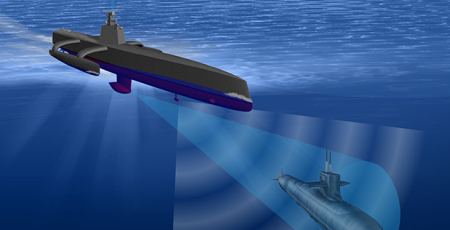
As nuclear blasts go, North Korea’s first test in 2006 was small. The detonation of an underground device produced an explosive force well below one kiloton (less than a tenth of the size of the bomb dropped on Hiroshima in 1945). Even so, the vibrations it caused were recorded half a world away in the centre of Africa. Advances in the sensitivity of seismic sensors and monitoring software are now good enough to distinguish between a distant nuclear detonation and, say, a building being demolished with conventional explosives, says Lassina Zerbo, head of the Preparatory Commission for the Comprehensive Test-Ban-Treaty Organisation (CTBTO), the international organisation that seeks to enforce the agreement ratified, so far, by 163 nations.
The CTBTO operates 170 seismic stations worldwide, 11 underwater hydroacoustic centres detecting sound waves in the oceans, 60 listening stations for atmospheric infrasound (low-frequency acoustic waves that can travel long distances) and 96 labs and radionuclide-sampling facilities. More sensors are being installed. Crucially, however, the optimal number for global coverage was recently reached. It is now impossible, reckons Dr Zerbo, to test even a small nuclear weapon in secret anywhere on Earth. And on top of that, the United States Air Force runs a detection network that includes satellites that can spot nuclear-weapons tests.
It is better, though, to discover a secret weapons programme before testing. Once a country has a nuclear bomb or two, there is not much other governments can do to stop it from making more, says Ilan Goldenberg, a former head of the Iran team at the Pentagon. Plenty of states want such capabilities. The Defence Science Board, an advisory body to the Pentagon, concluded in a report last year that the number of countries that might seek nuclear weapons is higher now than at any time since the cold war. Those states include Saudi Arabia and other Sunni-Arab rivals of Iran, which in July, after long and tortuous negotiations, signed a nuclear deal with America and other nations to restrict its nuclear activities, and to allow enhanced monitoring and inspection of its facilities.
As the technologies to unearth work on clandestine nuclear weapons become more diverse and more powerful, however, the odds of being detected are improving. Innovation is benefiting detection capabilities, says Ramesh Thakur, a former UN assistant secretary-general. The products under development range from spy software that sifts through electronic communications and financial transactions to new scanners that can detect even heavily shielded nuclear material….
Software used for this type of analysis include i2 Analyst’s Notebook from IBM, Palantir from a Californian firm of the same name, and ORA, which was developed with Pentagon funds at Carnegie Mellon University in Pennsylvania. ORA has crunched data on more than 30,000 nuclear experts’ work and institutional affiliations, research collaborations and academic publications, says Kathleen Carley, who leads the ORA work at Carnegie Mellon. Changes, such as a halt in publishing, can tell stories: scientists recruited into a weapons programme typically cannot publish freely. Greater insights appear when classified or publicly unavailable information is sifted too. Credit-card transactions can reveal that, say, a disproportionate number of doctors specialising in radiation poisoning are moving to the same area.
The software uses combinatorial mathematics, the analysis of combinations of discrete items, to score individuals on criteria including “centrality” (a person’s importance), “between-ness” (their access to others), and “degree” (the number of people they interact with). Network members with high between-ness and low degree tend to be central figures: they have access to lots of people, but like many senior figures may not interact with that many. Their removal messes things up for everybody. Five or more Iranian nuclear scientists assassinated in recent years—by Israel’s Mossad, some suspect—were no doubt chosen with help from such software, says Thomas Reed, a former secretary of the United States Air Force and co-author of “The Nuclear Express”, a history of proliferation.
Importantly, the software can also evaluate objects that might play a role in a nuclear programme. This is easier than it sounds, says a former analyst (who asked not to be named) at the Pentagon’s Central Command in Tampa, Florida. Ingredients for homemade conventional bombs and even biological weapons are available from many sources, but building nukes requires rare kit. The software can reveal a manageable number of “chokepoints” to monitor closely, he says. These include links, for instance, between the few firms that produce special ceramic composites for centrifuges and the handful of companies that process the material.
A number of countries, including Japan and Russia, use network analysis. Japan’s intelligence apparatus does so with help from the Ministry of Economy, Trade and Industry, which assists in deciding which “dual use” items that might have both peaceful and military purposes should not be exported. Such work is tricky, says a member of the advisory board (who also asked not to be named) to the security council of the Russian Federation, a body chaired by Vladimir Putin. Individual items might seem innocent enough, he says, and things can be mislabelled.
Data sources are diverse, so the work takes time. Intelligence often coalesces after a ship has left port, so foreign authorities are sometimes asked to board and search, says Rose Gottemoeller, undersecretary for arms control at America’s State Department. The speed of analysis is increasing, however. Software that converts phone conversations into computer-readable text has been “extremely helpful”, says John Carlson, a former head of the Australian foreign ministry’s Safeguards and Non-Proliferation Office.
Would-be nuclear states can also reduce their networks. North Korea helped to keep its centrifuge facility secret by using mostly black-market or domestically manufactured components. Iran is also indigenising its nuclear programme, which undermines what network analysis can reveal, says Alexander Montgomery, a political scientist at Reed College in Portland, Oregon. Iran mines uranium domestically and has produced centrifuge rotors with carbon fibre, instead of importing special maraging steel which is usually required.
A big computer system to make sense of all this would help, says Miriam John, vice-chairman of the Pentagon’s Threat Reduction Advisory Committee. Which is why the Pentagon is building one, called Constellation. Dr John describes it as a “fusion engine” that merges all sorts of data. For instance, computers can comb through years of satellite photos and infra-red readings of buildings to detect changes that might reveal nuclear facilities. Constellation aims to increase the value of such nuggets of information by joining them with myriad other findings. For example, the whereabouts of nuclear engineers who have stopped teaching before retirement age become more interesting if those people now happen to live within commuting distance of a suspect building.
Yet photographs and temperature readings taken from satellites, even in low Earth orbit, only reveal so much. With help from North Korea, Syria disguised construction of a nuclear reactor by assembling it inside a building in which the floor had been lowered. From the outside the roof line appeared to be too low to house such a facility. To sidestep the need for a cooling tower, water pipes ran underground to a reservoir near a river. The concealment was so good the site was discovered not with remote sensing but only thanks to human intelligence, says Dr Tobey, the former National Security Council official. (Israel bombed the building in 2007 before it could be completed.)
Some chemical emissions, such as traces of hydrofluoric acid and fluorine, can escape from even well-built enrichment facilities and, with certain sensors, have been detectable from space for about a decade, says Mr Carlson, the Australian expert. But detecting signs of enrichment via radiation emissions requires using different sorts of devices and getting much closer to suspected sources.
The “beauty” of neutrons and alpha, beta and gamma radiation, is that the energy levels involved also reveal if the source is fit for a weapon, says Kai Vetter, a physicist at the University of California, Berkeley. But air absorbs enough radiation from uranium and plutonium bomb fuel to render today’s detectors mostly useless unless they are placed just a few dozen metres away. (Radiological material for a “dirty bomb” made with conventional explosives is detectable much farther away.) Lead shielding makes detection even harder. Not one of the more than 20 confirmed cases of trafficking in bomb-usable uranium or plutonium has been discovered by a detector’s alarm, says Elena Sokova, head of the Vienna Centre for Disarmament and Non-Proliferation, a think-tank.
Ground-based detectors are becoming more sensitive….. Detectors still need to be close to whatever it is they are monitoring, which mostly restricts their use to transport nodes, such as ports and borders. The range the detectors operate over might stretch to about 100 metres in a decade or so, but this depends on uncertain advances in “active interrogation”—the bombardment of an object with high-energy neutrons or protons to produce other particles which are easier to pick up. One problem is that such detectors might harm stowaways hiding in cargo.
That risk has now been solved, claims Decision Sciences, a Californian company spun out of the Los Alamos National Laboratory in America. It uses 16,000 aluminium tubes containing a secret gas to record the trajectory of muons. These are charged particles created naturally in the atmosphere and which pass harmlessly through people and anything else in their path. However, materials deflect their path in different ways. By measuring their change in trajectory, a computer can identify, in just 90 seconds, plutonium and uranium as well as “drugs, tobacco, explosives, alcohol, people, fill in the blank”, says Jay Cohen, the company’s chief operating officer and a former chief of research for the United States Navy. The ability to unearth common contraband will make the machine’s $5m price tag more palatable for border officials. A prototype is being tested in Freeport, Bahamas.
Other groups are also working on muon detectors, some using technology developed for particle physics experiments at the Large Hadron Collider in Switzerland. Another approach involves detecting neutrinos, which are produced by the sun and nuclear reactors, and seeing how they interact with other forms of matter. The NNSA and other organisations are backing the construction of a prototype device called WATCHMAN in an old salt mine (to shield it from cosmic rays and other interference) in Painesville, Ohio. It will be used to detect neutrinos from limited plutonium production at a nuclear power station 13km away. Such a system might have a 1,000km range, eventually. But even that means it would require a friendly neighbour to house such a facility on the borders of a country being monitored.
Once nuclear facilities have been discovered, declared or made available for inspection as part of a deal, like that signed with Iran, the job of checking what is going on falls to experts from the UN’s International Atomic Energy Agency (IAEA). The equipment available to them is improving, too. The Canadian Nuclear Safety Commission has built a prototype hand-held spectrometer for determining if traces of uranium collected on a cotton swab and blasted with a laser emit a spectral signature that reveals enrichment beyond that allowed for generating electricity. Within three years it will provide an unprecedented ability to assess enrichment without shipping samples back to a lab, says Raoul Awad, director-general of security and safeguards at the commission.
Laser scanning can also reveal other signs of enrichment. A decade ago inspectors began scanning intricate centrifuge piping with surveying lasers. A change between visits can reveal any reconfiguration of the sort necessary for the higher levels of enrichment needed for bombmaking. Secret underground facilities might also be found by wheeling around new versions of ground-penetrating radar.
The remote monitoring of sites made available to inspectors is also getting better. Cameras used to record on videotape, which was prone to breaking—sometimes after less than three months’ use, says Julian Whichello, a former head of the IAEA’s surveillance unit. Today’s digital cameras last longer and they can be programmed to take additional pictures if any movement is detected or certain equipment is touched. Images are encrypted and stamped with sequential codes. If technicians at a monitored facility delete any pictures, the trickery will be noticed by software and the inspectors informed.
Such technology, however, only goes so far. The IAEA cannot inspect computers and countries can veto the use of some equipment. It does seem that inspectors sent to Iran will get access to Parchin, a site near Tehran where intelligence agencies say tests related to nuclear-weapons making took place. (Iran denies it has a military programme.) But even the best tech wizardry can only reveal so much when buildings have been demolished and earth moved, as in Parchin.
Could nuclear weapons be built in secret today? …. A senior American State Department counter-proliferation official (whose asked to remain anonymous), however, says that it is not impossible…Companies, including a General Electric consortium, are making progress enriching uranium with lasers . If this becomes practical, some worry that it might be possible to make the fuel for a nuclear bomb in smaller facilities with less fancy kit than centrifuges
Monitoring nuclear weapons: The nuke detectives, Economist Technology Quarterly, Sept. 5, 2015, at 10





 Ghana’s parliament on March 23, 2018 ratified a deal granting “unimpeded” access to the United States to deploy troops and military equipment in the West African nation in a vote boycotted by the opposition, legislators said.The Ghana-U.S. Military Cooperation agreement requires Ghana to provide unimpeded access to agreed facilities and areas to U.S. forces, their contractors and other related services.
Ghana’s parliament on March 23, 2018 ratified a deal granting “unimpeded” access to the United States to deploy troops and military equipment in the West African nation in a vote boycotted by the opposition, legislators said.The Ghana-U.S. Military Cooperation agreement requires Ghana to provide unimpeded access to agreed facilities and areas to U.S. forces, their contractors and other related services.
 The activity, hostile action that falls short of–but often precedes–violence, is sometimes referred to as gray zone warfare, the ‘zone’ being a sort of liminal state in between peace and war. The actors that work in it are difficult to identify and their aims hard to predict, by design…
The activity, hostile action that falls short of–but often precedes–violence, is sometimes referred to as gray zone warfare, the ‘zone’ being a sort of liminal state in between peace and war. The actors that work in it are difficult to identify and their aims hard to predict, by design…
 The Maldives archipelago, popular among luxury honeymooners, has become a playing field for geostrategic rivalry as China expands its influence in the Indian Ocean and the U.S. and India push back.
The Maldives archipelago, popular among luxury honeymooners, has become a playing field for geostrategic rivalry as China expands its influence in the Indian Ocean and the U.S. and India push back.
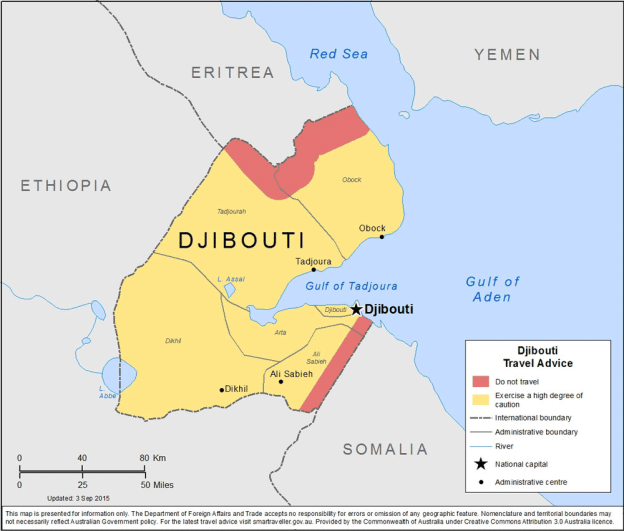
 The top US general for Africa told lawmakers the American military could face “significant” consequences should China take a key port in Djibouti…. In Febuary 2018, Djibouti ended its contract with Dubai’s DP World, one of the world’s biggest port operators, to run the Doraleh Container Terminal, citing failure to resolve a dispute that began in 2012. DP World called the move an illegal seizure of the terminal and said it had begun new arbitration proceedings before the London Court of International Arbitration.
The top US general for Africa told lawmakers the American military could face “significant” consequences should China take a key port in Djibouti…. In Febuary 2018, Djibouti ended its contract with Dubai’s DP World, one of the world’s biggest port operators, to run the Doraleh Container Terminal, citing failure to resolve a dispute that began in 2012. DP World called the move an illegal seizure of the terminal and said it had begun new arbitration proceedings before the London Court of International Arbitration.

 The world’s vast oceans and seas offer seemingly endless spaces in which adversaries of the United States can maneuver undetected. The U.S. military deploys networks of manned and unmanned platforms and sensors to monitor adversary activity, but the scale of the task is daunting and hardware alone cannot meet every need in the dynamic marine environment. Sea life, however, offers a potential new advantage. Marine organisms are highly attuned to their surroundings—their survival depends on it—and a new program out of DARPA’s Biological Technologies Office aims to tap into [marine animals] natural sensing capabilities to detect and signal when activities of interest occur in strategic waters such as straits and littoral regions.
The world’s vast oceans and seas offer seemingly endless spaces in which adversaries of the United States can maneuver undetected. The U.S. military deploys networks of manned and unmanned platforms and sensors to monitor adversary activity, but the scale of the task is daunting and hardware alone cannot meet every need in the dynamic marine environment. Sea life, however, offers a potential new advantage. Marine organisms are highly attuned to their surroundings—their survival depends on it—and a new program out of DARPA’s Biological Technologies Office aims to tap into [marine animals] natural sensing capabilities to detect and signal when activities of interest occur in strategic waters such as straits and littoral regions.



 The African Union on Friday urged Mauritania to make a greater effort to eliminate slavery after the country handed out lenient sentences to a family of slave owners in a landmark conviction….In a statement published online, the
The African Union on Friday urged Mauritania to make a greater effort to eliminate slavery after the country handed out lenient sentences to a family of slave owners in a landmark conviction….In a statement published online, the

 Mines planted during more than three years of war in Benghazi (2014-2017) are taking a high toll on under-equipped deminers and residents trying to return to districts where protracted battles took place. Military engineers striving to clear the explosives lack mine detectors and are working with basic tools and their bare hands. Their task is painstaking and extremely dangerous: 50 have been killed and 60 wounded, according to a military source.
Mines planted during more than three years of war in Benghazi (2014-2017) are taking a high toll on under-equipped deminers and residents trying to return to districts where protracted battles took place. Military engineers striving to clear the explosives lack mine detectors and are working with basic tools and their bare hands. Their task is painstaking and extremely dangerous: 50 have been killed and 60 wounded, according to a military source.

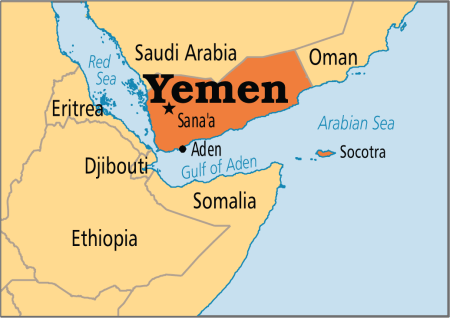
 A withering United Nations report on Yemen’s civil war provides fresh evidence about the extent to which Saudi Arabia and Iran have intervened in the conflict, pursuing their regional proxy war even as Yemen disintegrated into “warring statelets” that would be difficult to reunite. The U.N. panel said there were “strong indications of the supply of arms-related material manufactured in, or emanating from, the Islamic Republic of Iran,” in violation of a U.N. embargo on Yemen.
A withering United Nations report on Yemen’s civil war provides fresh evidence about the extent to which Saudi Arabia and Iran have intervened in the conflict, pursuing their regional proxy war even as Yemen disintegrated into “warring statelets” that would be difficult to reunite. The U.N. panel said there were “strong indications of the supply of arms-related material manufactured in, or emanating from, the Islamic Republic of Iran,” in violation of a U.N. embargo on Yemen.


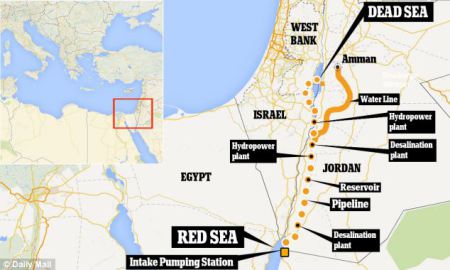
 The Dead Sea is dying. Half a century ago its hyper-salty, super-pungent waters stretched 80km from north to south. That has shrunk to just 48km at its longest point. The water level is falling by more than a meter per year. All but a trickle from its source, the Jordan River, is now used up before it reaches the sea. “It will never disappear, because it has underground supplies, but it will be like a small pond in a very big hole,” says Munqeth Mehyar of EcoPeace, an NGO.
The Dead Sea is dying. Half a century ago its hyper-salty, super-pungent waters stretched 80km from north to south. That has shrunk to just 48km at its longest point. The water level is falling by more than a meter per year. All but a trickle from its source, the Jordan River, is now used up before it reaches the sea. “It will never disappear, because it has underground supplies, but it will be like a small pond in a very big hole,” says Munqeth Mehyar of EcoPeace, an NGO.



 As the overthrow of despot Robert Mugabe entered a stalemate on November 17, 2017, eyes turned to China — Zimbabwe’s largest foreign investor and a key ally — amid speculation over its role in the military coup.Source in Harare believe the Zimbabwean conflict within the ruling party Zanu PF is involving two rival camps has direct links to China and Russia with both countries trying to control and protect their own economic interests.
As the overthrow of despot Robert Mugabe entered a stalemate on November 17, 2017, eyes turned to China — Zimbabwe’s largest foreign investor and a key ally — amid speculation over its role in the military coup.Source in Harare believe the Zimbabwean conflict within the ruling party Zanu PF is involving two rival camps has direct links to China and Russia with both countries trying to control and protect their own economic interests.
 When Doundou Chefou first took up arms as a youth a decade ago, it was for the same reason as other ethnic Fulani herders along the Niger-Mali border: to protect his livestock. He had nothing against the Republic of Niger, let alone the United States of America. His quarrel was with rival Tuareg cattle raiders.
When Doundou Chefou first took up arms as a youth a decade ago, it was for the same reason as other ethnic Fulani herders along the Niger-Mali border: to protect his livestock. He had nothing against the Republic of Niger, let alone the United States of America. His quarrel was with rival Tuareg cattle raiders.






 Two millivolts is enough to show that someone has seen something even before he knows he has seen it himself. The two millivolts in question are those associated with P300, a fleeting electrical signal produced by a human brain which has just recognised an object it has been seeking. Crucially, this signal is detectable by electrodes in contact with a person’s scalp before he is consciously aware of having recognised anything.
Two millivolts is enough to show that someone has seen something even before he knows he has seen it himself. The two millivolts in question are those associated with P300, a fleeting electrical signal produced by a human brain which has just recognised an object it has been seeking. Crucially, this signal is detectable by electrodes in contact with a person’s scalp before he is consciously aware of having recognised anything.



 South Carolina is suing the U.S. government to recover $100 million in fines it says the Department of Energy owes the state for failing to remove one metric ton of plutonium stored there. The lawsuit was filed on August 7, 2017.
South Carolina is suing the U.S. government to recover $100 million in fines it says the Department of Energy owes the state for failing to remove one metric ton of plutonium stored there. The lawsuit was filed on August 7, 2017.



 Seven months after Libyan forces defeated Islamic State in Sirte, hundreds of bodies of foreign militants are still stored in freezers as authorities negotiate with other governments to decide what to do with them, local officials say. The corpses have been shipped to Misrata, a city further to the west whose forces led the fight to defeat Islamic State in Sirte in December 2016.
Seven months after Libyan forces defeated Islamic State in Sirte, hundreds of bodies of foreign militants are still stored in freezers as authorities negotiate with other governments to decide what to do with them, local officials say. The corpses have been shipped to Misrata, a city further to the west whose forces led the fight to defeat Islamic State in Sirte in December 2016.




 On June 22nd 2017,
On June 22nd 2017, 




 A SpaceX Falcon rocket lifted off from the Kennedy Space Center in Florida on May , 2017 to boost a classified spy satellite into orbit for the U.S. military, then turned around and touched down at a nearby landing pad.
A SpaceX Falcon rocket lifted off from the Kennedy Space Center in Florida on May , 2017 to boost a classified spy satellite into orbit for the U.S. military, then turned around and touched down at a nearby landing pad.

 A real-estate magnate is financing Google’s and Facebook Inc.’s new trans-Pacific internet cable, the first such project that will be majority-owned by a single Chinese company. Wei Junkang, 56, is the main financier of the cable between Los Angeles and Hong Kong, a reflection of growing interest from China’s investors in high-tech industries. It will be the world’s highest-capacity internet link between Asia and the U.S.
A real-estate magnate is financing Google’s and Facebook Inc.’s new trans-Pacific internet cable, the first such project that will be majority-owned by a single Chinese company. Wei Junkang, 56, is the main financier of the cable between Los Angeles and Hong Kong, a reflection of growing interest from China’s investors in high-tech industries. It will be the world’s highest-capacity internet link between Asia and the U.S.


 On 7 March 2017, WikiLeaks began its new series of leaks on the U.S. Central Intelligence Agency…code-named “Vault 7” by WikiLeaks..
On 7 March 2017, WikiLeaks began its new series of leaks on the U.S. Central Intelligence Agency…code-named “Vault 7” by WikiLeaks..