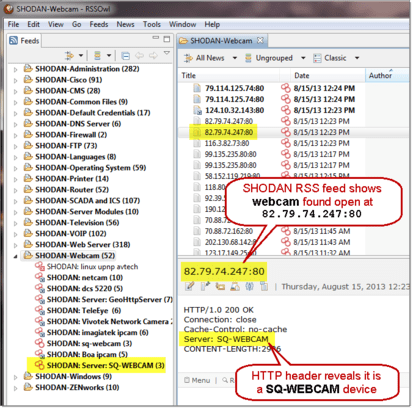
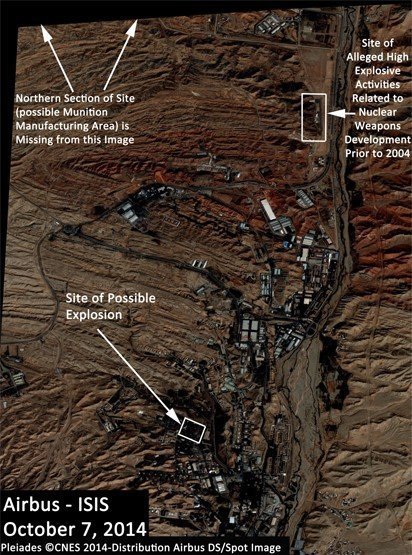
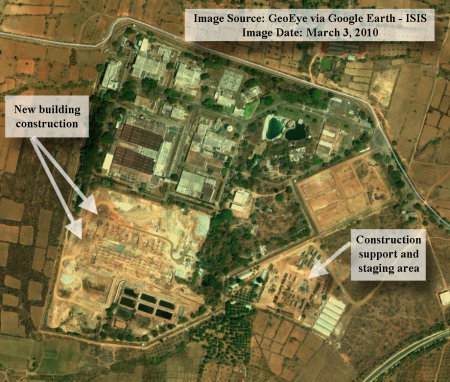
To help push Soviet forces out of Afghanistan in the 1980s, America’s Central Intelligence Agency (CIA) gave Afghan fighters shoulder-launched Stinger anti-aircraft missiles. Accurate and easy-to-use, the Stingers caused grievous losses. But after the Soviet withdrawal in 1989, the CIA wanted to discourage the use of the leftover missiles. It got hold of some of those circulating on the black market and booby-trapped them, so that anyone who tried to fire one would have his head blown off. The aim, according to a former CIA official, was to deter both the sale and use of the remaining missiles…
[Today] technological tweaks may be able to help limit the spread and use of small arms, making possible weapons that stop working after a certain period of time, or can only be used by specific people or in particular places. Proponents of such technologies believe they have the potential to succeed where political and legislative attempts at arms control have failed. Perhaps the simplest approach is the use of technological tricks that shorten weapons’ lifespans. “Self-deactivating” landmines, for example, will not detonate after their battery runs down. They have been adopted by America and some of its allies, but constitute only a tiny fraction of mines deployed around the world. In a similar vein, one proposal is that launchers for shoulder-fired missiles should only work with a uniquely configured, non-rechargeable battery manufactured in a single, tightly controlled plant. This would, in theory, limit the lifespan of the weapons for anyone without access to new batteries. But there would be workarounds. This year rebels in Syria posted video online of a portable missile-launcher rigged to an external power supply for target acquisition. It fired a missile that shot down a helicopter near the Abu ad-Duhur military airbase, south of Aleppo. Similarly rigged missiles have been fired by Hamas militants at Israeli aircraft.
Shoulder-fired missiles, RPGs, mortars, and guided anti-tank missiles could also be made to stop working after a while by engineering their chemical propellants to become inert after a predetermined period, says Patrick McCarthy, head of a UN project called the International Small Arms Control Standards. It is hardly likely that governments would buy perishable weapons of the sort for their own use, but rebel groups might accept them from a sympathetic country, at least if nothing better were on offer. This might also allay fears in the donor country that the weapons might end up in undesirable hands many years later.
A second approach to arms control is to track weapons electronically. Almost all illicit small arms were legally manufactured or imported and were later diverted, often with help from corrupt officials and forged documents. Discreet monitoring and tracking of shipping containers carrying weapons makes it harder to steal or reroute them. Jim Giermanski, a former US Air Force colonel, says America’s Defence Department recently began shipping to Afghanistan, on commercial vessels, containers capable of reporting an opened door, vibrations from a break-in attempt and their location, derived from global positioning system (GPS) satellites. A container can, in essence, “report its own hijacking”, says Dr Giermanski, now boss of Powers International, a company based in North Carolina that helps shippers adopt the tracking technology. It is just now becoming practical and inexpensive enough for wide use, he says.
In some cases it is even possible to track individual weapons by building in a transmitter that regularly signals their precise co-ordinates. This is already done for larger weapons deemed “expensive enough and consequential enough”, says Lincoln Bloomfield, a former State Department official for military and political affairs who served as a special envoy under George Bush junior. Doing the same for small arms would be expensive, but the transmitter could be cleverly attached so that removing it disables the weapon.
In RPGs, a GPS transmitter could be concealed in a grip assembly, says Jean-Marc Anzian Kouadja, executive secretary of the National Commission of Small Arms and Light Weapons at Côte d’Ivoire’s interior ministry. Wrench it out, he says, and you break the trigger mechanism. Governments might be willing to foot the bill to secure their stockpiles from insurgent raids or managers who might otherwise cut deals with gunrunners. But a problem, he notes, is that cyber-savvy rebels might work out how to use the technology to track government troops…
Tracking weapons can be done without satellites, however. Some armies have started using tiny radio-frequency identification (RFID) chips, like those found in contactless credit cards and public-transport tickets, which do not require batteries to operate. Instead, when they are passed close to a reader (when passing through a door, for example), the chips absorb enough radio energy to power up and transmit a short burst of identification data. Weapons passing in and out of an armoury can thus be tracked. SkyRFID, a company based in Ontario, notes that its weaponry tags are not damaged by vibration, grime or cleaning solvents. Replacing manual logging makes it harder for armoury staff to pretend munitions sold on the sly are still in stock. (A UN report on improving marking and tracing technologies is due to be published in April 2014.)
Another alternative to GPS transmitters would be to track weapons by outfitting them with the inexpensive SIM cards that allow mobile-phone networks to identify subscribers. A weapon would communicate with nearby mobile-network towers to indicate its position within a rough area, says Mr Kalbusch. And a system of this sort could, in theory, form the basis of a “remote control” feature, allowing weapons to be disabled from a distance.
“Kill switches” or “backdoors”, as these features are sometimes known, have so far been associated with expensive weapon systems that must send and receive data to operate. David Kay, America’s most senior arms inspector in post-Saddam Iraq, has noted that one of the reasons why Russia’s best air-defence systems have not been installed in Iran is probably because the Iranians fear that Russia might be capable of countermanding missile launches against certain countries’ aircraft. Now similar “override” systems are being applied to small arms, too.
TriggerSmart, a company based in Limerick, Ireland, has developed a motorised mechanism that can block or unblock the trigger of an assault rifle. It is controlled not by a switch on the weapon itself, but rather by a command sent from an aircraft, satellite, mobile-network tower or radio station. Weighing less than 30 grams (including a standard AAA battery), the mechanism allows an “offending weapon” to be remotely disabled, says Patrick O’Shaughnessy, TriggerSmart’s head of research and development. It costs about $150 to retrofit an existing rifle or build the technology into a new one.
The biggest buyers, Mr O’Shaughnessy reckons, will be armies that work with foreign security forces. American officials have expressed interest. One in six of the Western troops killed last year in Afghanistan was slain in an “insider attack” by a partner in the country’s security forces. TriggerSmart’s technology could allow any member of a unit to block the use of firearms by partner forces. But being expected to use weapons that can be remotely disabled hardly seems likely to engender trust. And it would be impractical to introduce light-weaponry override systems in their current form for large numbers of soldiers or police, says Richard Rowe, a retired US Army major-general who oversaw the instruction and equipping of 550,000 Iraqi security recruits.
Even with further technological advances, few armies will be eager to adopt such kit, Mr Kalbusch says. Governments would worry that their arsenals could be neutered by an adversary, or, more straightforwardly, by the country that supplied the arms. Attempts to mandate use of the technology seem unlikely to succeed, because small arms are made in many countries. And sometimes foreign powers want rebels to steal a government’s weapons and use them against it, as Western-supported opponents of Libya’s Qaddafi regime did in 2011.
Away from the battlefield, other arms-control technologies are being developed to prevent the unintended or unauthorised use of weapons belonging to civilians or police officers. In the decade to 2010, 1,217 American minors were killed in accidental shootings, according to the most recent data from the Centres for Disease Control. And it is not uncommon for a police officer to be shot with a service weapon that has been wrested away. Accordingly, new “personalised” firearms are being developed which fire only when held by the owner or another authorised person, with the specific aim of preventing a gun owner (and his family or co-workers) from being killed with his own weapon. Because the verification takes place within the weapon itself, its backers note, the technology is more likely to be accepted than remote-override features on military weapons… One example is a .22-calibre pistol called iP1 made by Armatix, a German firm. It only fires if the shooter is wearing a special wristwatch containing an RFID chip, which is detected by the gun. If the gun is more than 40 centimetres from the RFID chip, its trigger locks. Attempting to disable the trigger lock destroys the iP1 “irrevocably”, according to Maximilian Hefner, the firm’s boss. The list price is $1,699.
A similar system for shotguns, called M-2000, has been developed by iGun Technology Corporation, based in Florida. When an RFID chip embedded in a ring is brought near the shotgun, a solenoid switch instantly unlocks the trigger. (Alternatively, the chip could be surgically implanted in the owner’s hand.) The system is seamless, according to Jonathan Mossberg, the firm’s founder. “You pick up the gun, pull the trigger, it goes boom—no thought involved,” he says. The battery inside the gun that powers the RFID reader lasts for more than eight years, and it sounds a warning alarm after six years. It costs about $200 to add to a firearm.
A wristwatch or a ring could be stolen, however, so other smart guns rely instead on biometric characteristics of their owner’s body, such as a fingerprint. The New Jersey Institute of Technology has devised a personalised Beretta pistol. When its magnetic trigger is pulled past a sensor in the trigger guard, a chip is switched on to crunch data from pressure-sensing piezoelectric sensors in the handgrip. Only if they match the owner’s bone geometry and “grip dynamics” does the trigger unlock. All this happens within the tenth of a second it takes to pull the trigger all the way back. The system is not foolproof: on average, around 1% of people with the same hand size will be able to fire a gun personalised for a particular user. But a gun set up for an adult cannot be fired by a child. The US Army is testing the system at an armaments laboratory in Picatinny, New Jersey.
Firearms that are unlocked with a fingerprint reader have been developed by Kodiak Industries, based in Utah, and Safe Gun Technology, based in Georgia. Biomac Systems, a firm based in Los Angeles, California and Ferlach, Austria, is designing a biometric kit to retrofit pistols. Barack Obama has encouraged the development of such technologies and has directed America’s attorney general to review them. Smart-gun technology also received a boost last year when it won the fictional endorsement of James Bond in “Skyfall”. Issued a gun coded to his palmprint that only he can fire, Bond is told that it is “less of a random killing machine, more of a personal statement”.
And yet demand looks weak, especially in America, by far the biggest market for civilian firearms: the iGun M-2000 failed to sell at all. Maxim Popenker, an author of firearm reference books based in St Petersburg, Russia, observes that sooner or later a bad guy will shoot a good guy because the latter’s personalised gun refuses to fire due to “gloves, dirt, sweat, blood or stress”. Gun enthusiasts have raised similar objections: personalised smart guns are simply less effective for self-defence, they argue, because of the risk that the safety technology will fail to work properly. Triggers could be unlocked by voice, but this risks betraying the position of someone hiding.
Smart weapons: Kill switches and safety catches, Economist, Nov. 30, 2013, at 11
.


































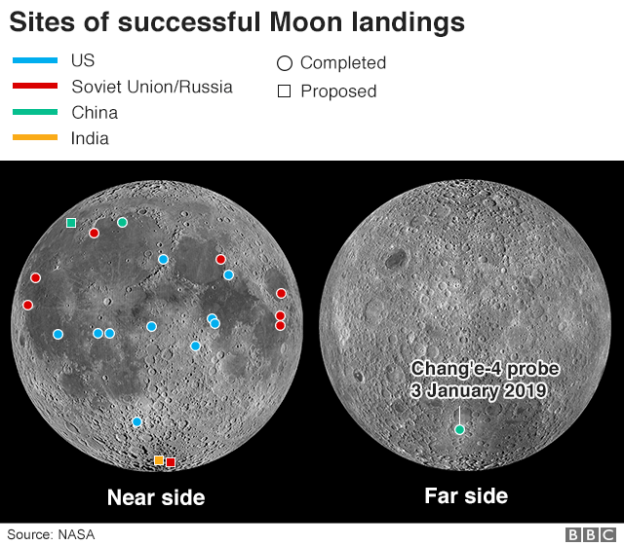





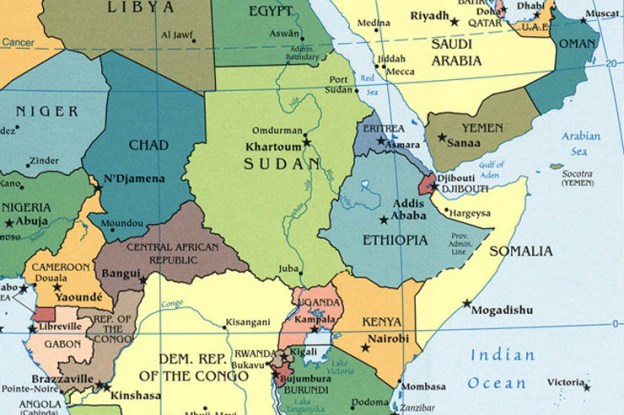
 The rulers of United Arab Emirates (UAE), one of whose components, Dubai, own a majority stake in DP World, one of the world’s largest maritime firms with perations in 40 countries.It is one of several Gulf states trying to gain a strategic foothold in east Africa through ports. Controlling these offers commercial and military advantages but risks exacerbating tensions in the region…
The rulers of United Arab Emirates (UAE), one of whose components, Dubai, own a majority stake in DP World, one of the world’s largest maritime firms with perations in 40 countries.It is one of several Gulf states trying to gain a strategic foothold in east Africa through ports. Controlling these offers commercial and military advantages but risks exacerbating tensions in the region…


 A Beijing-funded wharf in Vanuatu is big enough to allow powerful warships to dock alongside it, heightening fears the port could be converted into a Chinese naval installation. Fairfax Media inspected the $114 million Luganville wharf and was told US coastguard officials and Marines recently visited the sprawling facility and took a keen interest in its specifications. The Chinese and Vanuatu governments have strenuously denied they have discussed a military base…
A Beijing-funded wharf in Vanuatu is big enough to allow powerful warships to dock alongside it, heightening fears the port could be converted into a Chinese naval installation. Fairfax Media inspected the $114 million Luganville wharf and was told US coastguard officials and Marines recently visited the sprawling facility and took a keen interest in its specifications. The Chinese and Vanuatu governments have strenuously denied they have discussed a military base…
 The
The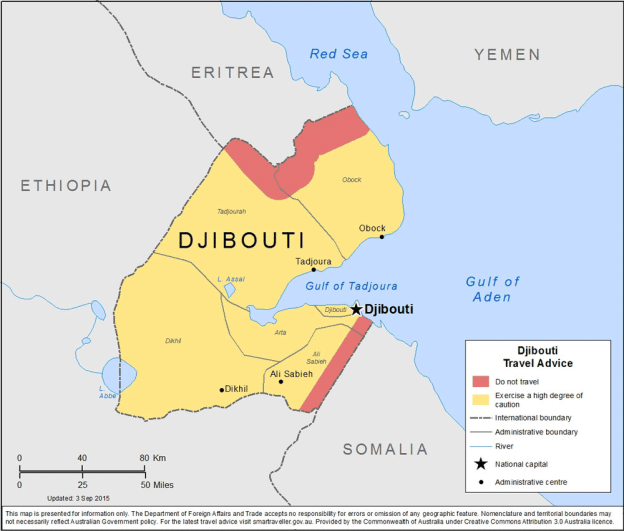
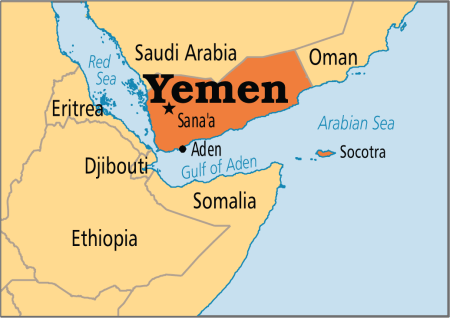
 The top US general for Africa told lawmakers the American military could face “significant” consequences should China take a key port in Djibouti…. In Febuary 2018, Djibouti ended its contract with Dubai’s DP World, one of the world’s biggest port operators, to run the Doraleh Container Terminal, citing failure to resolve a dispute that began in 2012. DP World called the move an illegal seizure of the terminal and said it had begun new arbitration proceedings before the London Court of International Arbitration.
The top US general for Africa told lawmakers the American military could face “significant” consequences should China take a key port in Djibouti…. In Febuary 2018, Djibouti ended its contract with Dubai’s DP World, one of the world’s biggest port operators, to run the Doraleh Container Terminal, citing failure to resolve a dispute that began in 2012. DP World called the move an illegal seizure of the terminal and said it had begun new arbitration proceedings before the London Court of International Arbitration.

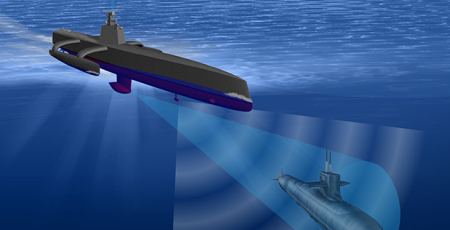
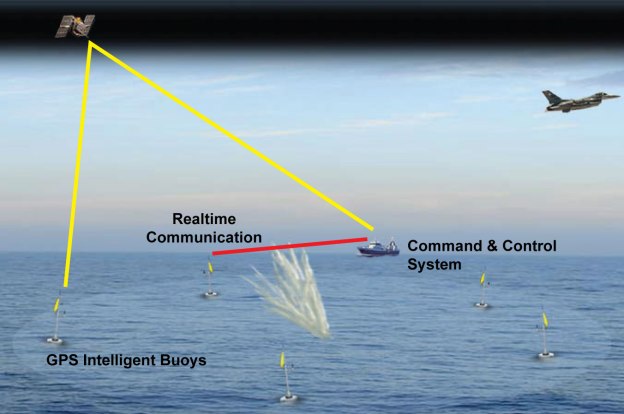
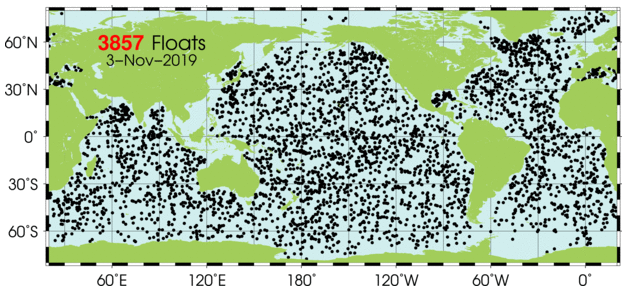
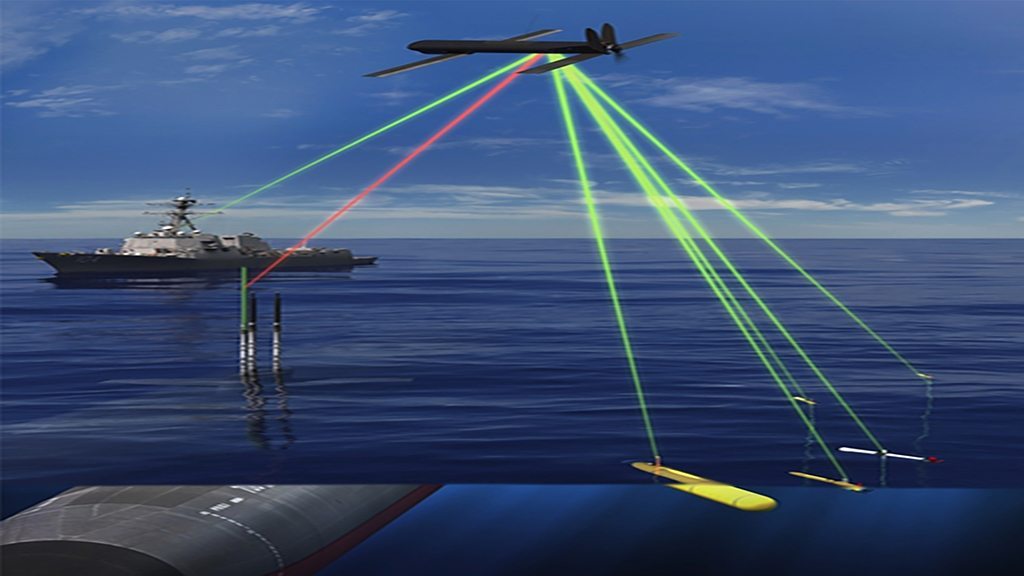
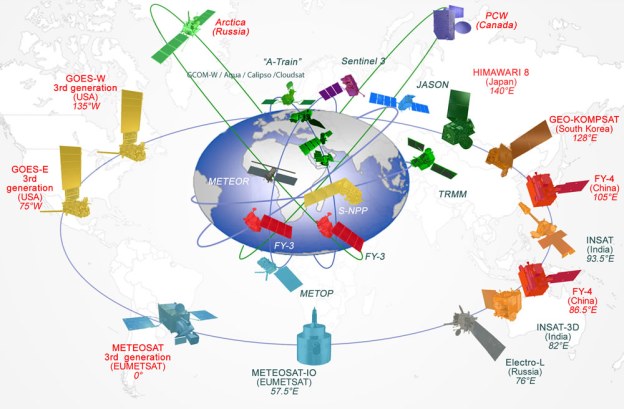
 The world’s vast oceans and seas offer seemingly endless spaces in which adversaries of the United States can maneuver undetected. The U.S. military deploys networks of manned and unmanned platforms and sensors to monitor adversary activity, but the scale of the task is daunting and hardware alone cannot meet every need in the dynamic marine environment. Sea life, however, offers a potential new advantage. Marine organisms are highly attuned to their surroundings—their survival depends on it—and a new program out of DARPA’s Biological Technologies Office aims to tap into [marine animals] natural sensing capabilities to detect and signal when activities of interest occur in strategic waters such as straits and littoral regions.
The world’s vast oceans and seas offer seemingly endless spaces in which adversaries of the United States can maneuver undetected. The U.S. military deploys networks of manned and unmanned platforms and sensors to monitor adversary activity, but the scale of the task is daunting and hardware alone cannot meet every need in the dynamic marine environment. Sea life, however, offers a potential new advantage. Marine organisms are highly attuned to their surroundings—their survival depends on it—and a new program out of DARPA’s Biological Technologies Office aims to tap into [marine animals] natural sensing capabilities to detect and signal when activities of interest occur in strategic waters such as straits and littoral regions.






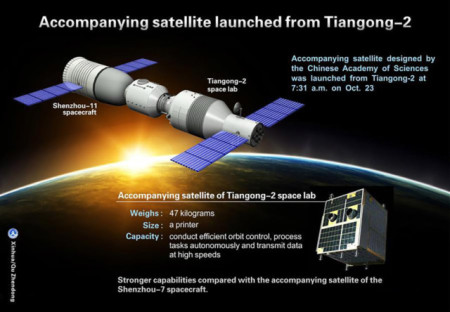
 A SpaceX Falcon rocket lifted off from the Kennedy Space Center in Florida on May , 2017 to boost a classified spy satellite into orbit for the U.S. military, then turned around and touched down at a nearby landing pad.
A SpaceX Falcon rocket lifted off from the Kennedy Space Center in Florida on May , 2017 to boost a classified spy satellite into orbit for the U.S. military, then turned around and touched down at a nearby landing pad.
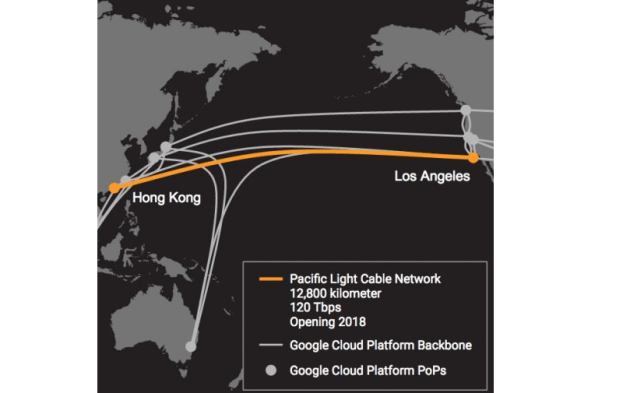
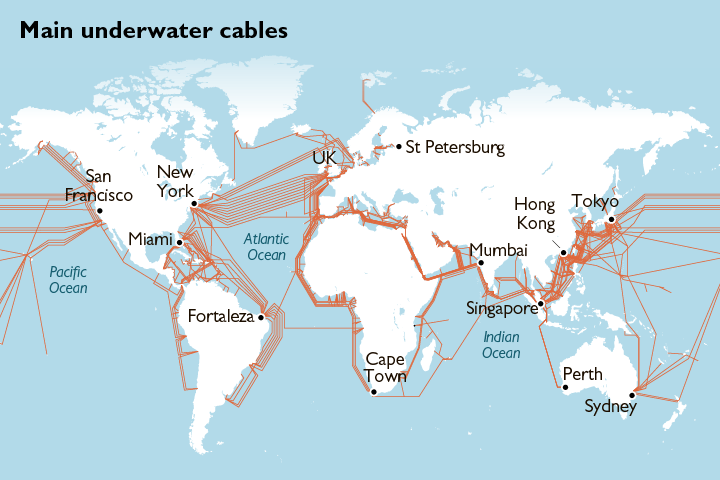
 A real-estate magnate is financing Google’s and Facebook Inc.’s new trans-Pacific internet cable, the first such project that will be majority-owned by a single Chinese company. Wei Junkang, 56, is the main financier of the cable between Los Angeles and Hong Kong, a reflection of growing interest from China’s investors in high-tech industries. It will be the world’s highest-capacity internet link between Asia and the U.S.
A real-estate magnate is financing Google’s and Facebook Inc.’s new trans-Pacific internet cable, the first such project that will be majority-owned by a single Chinese company. Wei Junkang, 56, is the main financier of the cable between Los Angeles and Hong Kong, a reflection of growing interest from China’s investors in high-tech industries. It will be the world’s highest-capacity internet link between Asia and the U.S.