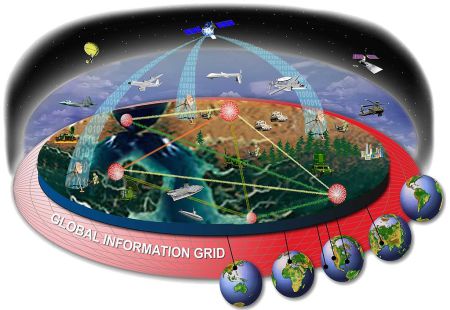
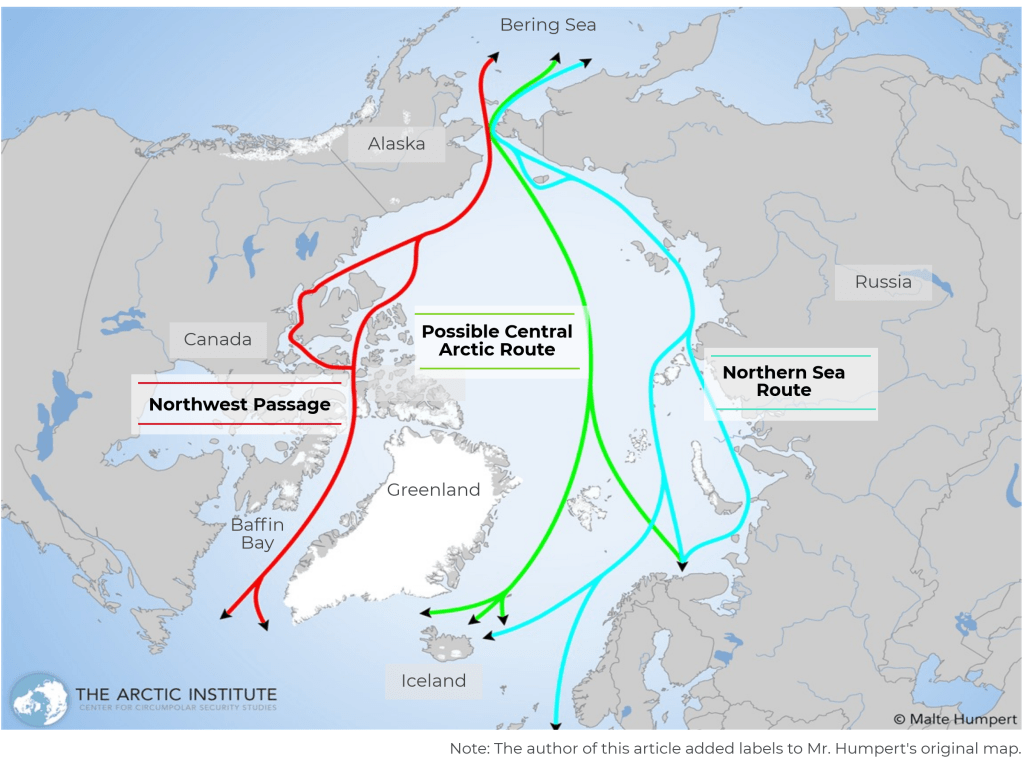
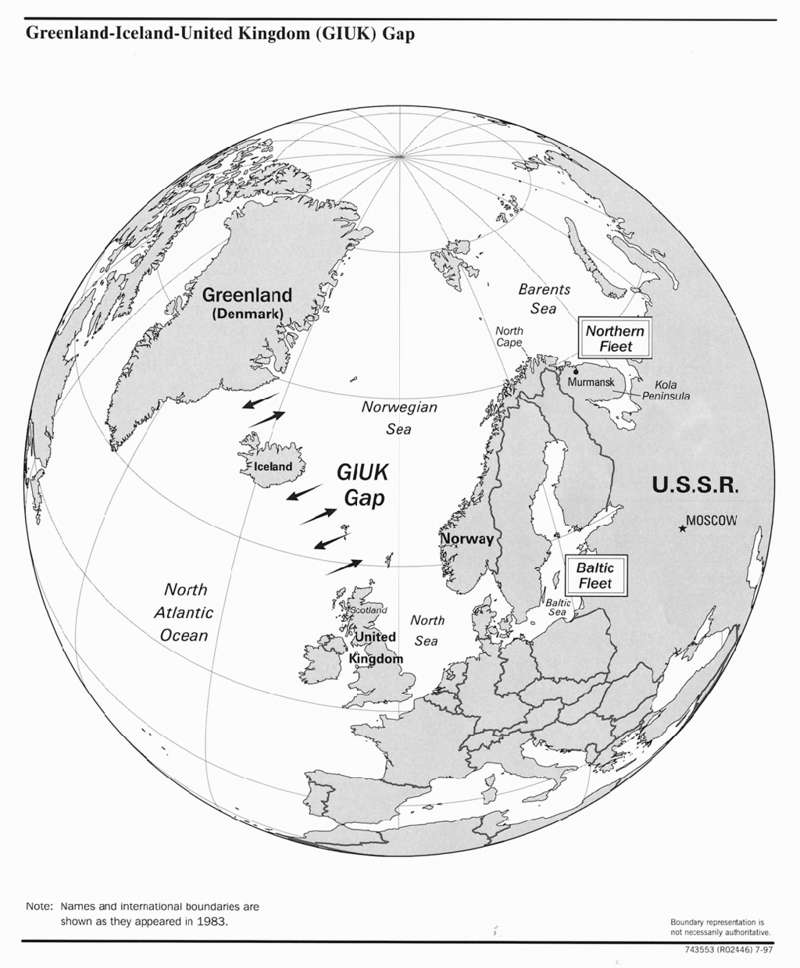
The United States [is developing] a “third offset strategy”… It is the third time since the second world war that America has sought technological breakthroughs to offset the advantages of potential foes and reassure its friends. The first offset strategy occurred in the early 1950s, when the Soviet Union was fielding far larger conventional forces in Europe than America and its allies could hope to repel. The answer was to extend America’s lead in nuclear weapons to counter the Soviet numerical advantage—a strategy known as the “New Look”.
A second offset strategy was conceived in the mid-1970s. American military planners, reeling from the psychological defeat of the Vietnam war, recognised that the Soviet Union had managed to build an equally terrifying nuclear arsenal. They had to find another way to restore credible deterrence in Europe. Daringly, America responded by investing in a family of untried technologies aimed at destroying enemy forces well behind the front line. Precision-guided missiles, the networked battlefield, reconnaissance satellites, the Global Positioning System (GPS) and radar-beating “stealth” aircraft were among the fruits of that research…The second offset strategy, the so-called “revolution in military affairs” was hammered home in 1991 during the first Gulf war. Iraqi military bunkers were reduced to rubble and Soviet-style armoured formations became sitting ducks. Watchful Chinese strategists, who were as shocked as their Soviet counterparts had been, were determined to learn from it.
The large lead that America enjoyed then has dwindled. Although the Pentagon has greatly refined and improved the technologies that were used in the first Gulf war, these technologies have also proliferated and become far cheaper. Colossal computational power, rapid data processing, sophisticated sensors and bandwidth—some of the components of the second offset—are all now widely available.
And America has been distracted. During 13 years of counter-insurgency and stabilisation missions in Afghanistan and Iraq, the Pentagon was more focused on churning out mine-resistant armoured cars and surveillance drones than on the kind of game-changing innovation needed to keep well ahead of military competitors. America’s combat aircraft are 28 years old, on average. Only now is the fleet being recapitalised with the expensive and only semi-stealthy F-35 Joint Strike Fighter. China, in particular, has seized the opportunity to catch up. With a defence budget that tends to grow by more than 10% a year, it has invested in an arsenal of precision short- to medium-range ballistic and cruise missiles, submarines equipped with wake-homing torpedoes and long-range anti-ship missiles, electronic warfare, anti-satellite weapons, modern fighter jets, integrated air defences and sophisticated command, control and communications systems.
The Chinese call their objective “winning a local war in high-tech conditions”. In effect, China aims to make it too dangerous for American aircraft-carriers to operate within the so-called first island chain (thus pushing them out beyond the combat range of their tactical aircraft) and to threaten American bases in Okinawa and South Korea. American strategists call it “anti-access/area denial”, or A2/AD. The concern for America’s allies in the region is that, as China’s military clout grows, the risks entailed in defending them from bullying or a sudden aggressive act—a grab of disputed islands to claim mineral rights, say, or a threat to Taiwan’s sovereignty—will become greater than an American president could bear. Some countries might then decide to throw in their lot with the regional hegemon.
Although China is moving exceptionally quickly, Russia too is modernising its forces after more than a decade of neglect. Increasingly, it can deploy similar systems. Iran and North Korea are building A2/AD capabilities too, albeit on a smaller scale than China. Even non-state actors such as Hizbullah in Lebanon and Islamic State in Syria and Iraq are acquiring some of the capabilities that until recently were the preserve of military powers.
Hence the need to come up with a third offset strategy.….America needs to develop new military technologies that will impose large costs on its adversaries
The programme needs to overcome at least five critical vulnerabilities.
- The first is that carriers and other surface vessels can now be tracked and hit by missiles at ranges from the enemy’s shore which could prevent the use of their cruise missiles or their tactical aircraft without in-flight refuelling by lumbering tankers that can be picked off by hostile fighters.
- The second is that defending close-in regional air bases from a surprise attack in the opening stages of a conflict is increasingly hard.
- Third, aircraft operating at the limits of their combat range would struggle to identify and target mobile missile launchers.
- Fourth, modern air defences can shoot down non-stealthy aircraft at long distances.
- Finally, the satellites America requires for surveillance and intelligence are no longer safe from attack.
It is an alarming list. Yet America has considerable advantages…. Those advantages include unmanned systems, stealthy aircraft, undersea warfare and the complex systems engineering that is required to make everything work together.
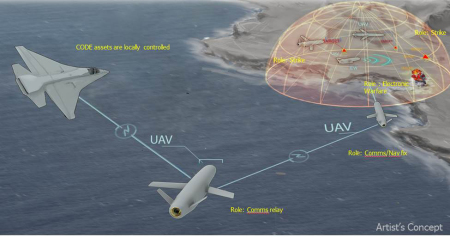
Over the next decade or so, America will aim to field unmanned combat aircraft that are stealthy enough to penetrate the best air defences and have the range and endurance to pursue mobile targets. Because they have no human pilots, fewer are needed for training. Since they do not need to rest, they can fly more missions back to back. And small, cheaper American drones might be used to swarm enemy air defences.
Drones are widespread these days, but America has nearly two decades of experience operating them. And the new ones will be nothing like the vulnerable Predators and Reapers that have been used to kill terrorists in Yemen and Waziristan. Evolving from prototypes like the navy’s “flying wing” X-47B and the air force’s RQ-180, they will be designed to survive in the most hostile environments. The more autonomous they are, the less they will have to rely on the control systems that enemies will try to disrupt—though autonomy also raises knotty ethical and legal issues.
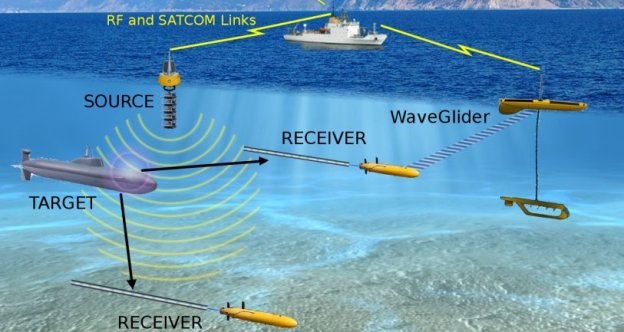
Some of the same technologies could be introduced to unmanned underwater vehicles. These could be used to clear mines, hunt enemy submarines in shallow waters, for spying and for resupplying manned submarines, for example, with additional missiles. They can stay dormant for long periods before being activated for reconnaissance or strike missions. Big technical challenges will have to be overcome:.. [T]he vehicles will require high-density energy packs and deep undersea communications.
Contracts will be awarded this summer for a long-range strike bomber, the first new bomber since the exotic and expensive B-2 began service two decades ago. The B-3, of which about 100 are likely to be ordered, will also have a stealthy, flying-wing design…
If surface vessels, particularly aircraft-carriers, are to remain relevant, they will need to be able to defend themselves against sustained attack from precision-guided missiles. The navy’s Aegis anti-ballistic missile-defence system is capable but expensive: each one costs $20m or so. If several of them were fired to destroy an incoming Chinese DF-21D anti-ship ballistic missile, the cost for the defenders might be ten times as much as for the attackers.
If carriers are to stay in the game, the navy will have to reverse that ratio. Hopes are being placed in two technologies: electromagnetic rail guns, which fire projectiles using electricity instead of chemical propellants at 4,500mph to the edge of space, and so-called directed-energy weapons, most likely powerful lasers. The rail guns are being developed to counter ballistic missile warheads; the lasers could protect against hypersonic cruise missiles. In trials, shots from the lasers cost only a few cents. The navy has told defence contractors that it wants to have operational rail guns within ten years.
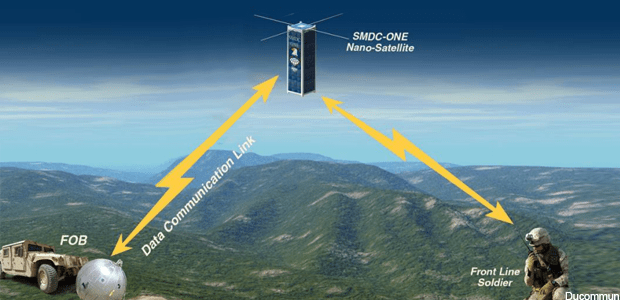
Defending against salvoes of incoming missiles will remain tricky and depend on other technological improvements, such as compact long-range radars that can track multiple targets. Finding ways to protect communications networks, including space-based ones, against attack is another priority. Satellites can be blinded by lasers or disabled by exploding missiles. One option would be to use more robust technologies to transmit data—such as chains of high-altitude, long-endurance drones operating in relays….
As Elbridge Colby of the Centre for a New American Security argues: “The more successful the offset strategy is in extending US conventional advantages, the more attractive US adversaries will find strategies of nuclear escalation.” The enemy always gets a vote.
Weapons Technology: Who’s Afraid of America, Economist, June 13, 2015, at 57.


































































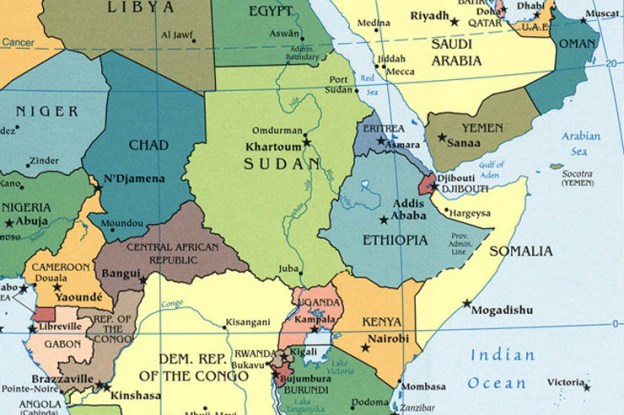
 The rulers of United Arab Emirates (UAE), one of whose components, Dubai, own a majority stake in DP World, one of the world’s largest maritime firms with perations in 40 countries.It is one of several Gulf states trying to gain a strategic foothold in east Africa through ports. Controlling these offers commercial and military advantages but risks exacerbating tensions in the region…
The rulers of United Arab Emirates (UAE), one of whose components, Dubai, own a majority stake in DP World, one of the world’s largest maritime firms with perations in 40 countries.It is one of several Gulf states trying to gain a strategic foothold in east Africa through ports. Controlling these offers commercial and military advantages but risks exacerbating tensions in the region…



 In 2009, coalition casualties in Afghanistan had as much as doubled in the space of a year. Civilian casualties climbed to 2412. It was 2009. Coalition forces had been there since 2001 with no end and, to this point, no real campaign plan in sight…
In 2009, coalition casualties in Afghanistan had as much as doubled in the space of a year. Civilian casualties climbed to 2412. It was 2009. Coalition forces had been there since 2001 with no end and, to this point, no real campaign plan in sight…


 The head of the U.S. Departement of Homeland Security (DHS) on May 15, 2018 told Congress that the agency needs new legal authority to track threatening drones and disable or destroy them if necessary. “Our enemies are exploring other technologies, too, such as drones, to put our country in danger. ISIS has used armed drones to strike targets in Syria, and we are increasingly concerned that they will try the same tactic on our soil,” she said…
The head of the U.S. Departement of Homeland Security (DHS) on May 15, 2018 told Congress that the agency needs new legal authority to track threatening drones and disable or destroy them if necessary. “Our enemies are exploring other technologies, too, such as drones, to put our country in danger. ISIS has used armed drones to strike targets in Syria, and we are increasingly concerned that they will try the same tactic on our soil,” she said…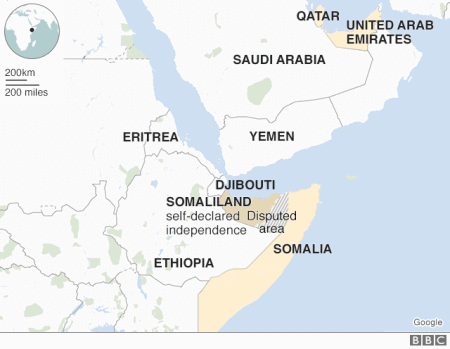
 A battle for access to seaports is underway in one of the world’s unlikeliest places: Somalia, now caught in a regional struggle between Saudi Arabia and the United Arab Emirates on one side with Qatar backed by Turkey on the other. At stake: not just the busy waters off the Somali coast but the future stability of the country itself.
A battle for access to seaports is underway in one of the world’s unlikeliest places: Somalia, now caught in a regional struggle between Saudi Arabia and the United Arab Emirates on one side with Qatar backed by Turkey on the other. At stake: not just the busy waters off the Somali coast but the future stability of the country itself.

 Ghana’s parliament on March 23, 2018 ratified a deal granting “unimpeded” access to the United States to deploy troops and military equipment in the West African nation in a vote boycotted by the opposition, legislators said.The Ghana-U.S. Military Cooperation agreement requires Ghana to provide unimpeded access to agreed facilities and areas to U.S. forces, their contractors and other related services.
Ghana’s parliament on March 23, 2018 ratified a deal granting “unimpeded” access to the United States to deploy troops and military equipment in the West African nation in a vote boycotted by the opposition, legislators said.The Ghana-U.S. Military Cooperation agreement requires Ghana to provide unimpeded access to agreed facilities and areas to U.S. forces, their contractors and other related services.
 The activity, hostile action that falls short of–but often precedes–violence, is sometimes referred to as gray zone warfare, the ‘zone’ being a sort of liminal state in between peace and war. The actors that work in it are difficult to identify and their aims hard to predict, by design…
The activity, hostile action that falls short of–but often precedes–violence, is sometimes referred to as gray zone warfare, the ‘zone’ being a sort of liminal state in between peace and war. The actors that work in it are difficult to identify and their aims hard to predict, by design…
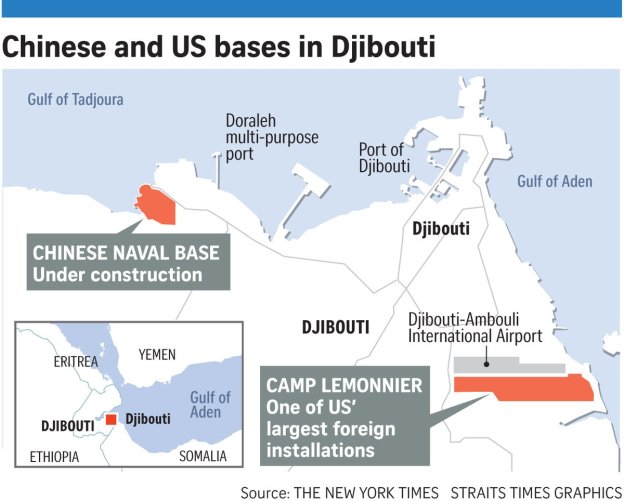
 The top US general for Africa told lawmakers the American military could face “significant” consequences should China take a key port in Djibouti…. In Febuary 2018, Djibouti ended its contract with Dubai’s DP World, one of the world’s biggest port operators, to run the Doraleh Container Terminal, citing failure to resolve a dispute that began in 2012. DP World called the move an illegal seizure of the terminal and said it had begun new arbitration proceedings before the London Court of International Arbitration.
The top US general for Africa told lawmakers the American military could face “significant” consequences should China take a key port in Djibouti…. In Febuary 2018, Djibouti ended its contract with Dubai’s DP World, one of the world’s biggest port operators, to run the Doraleh Container Terminal, citing failure to resolve a dispute that began in 2012. DP World called the move an illegal seizure of the terminal and said it had begun new arbitration proceedings before the London Court of International Arbitration.

 The world’s vast oceans and seas offer seemingly endless spaces in which adversaries of the United States can maneuver undetected. The U.S. military deploys networks of manned and unmanned platforms and sensors to monitor adversary activity, but the scale of the task is daunting and hardware alone cannot meet every need in the dynamic marine environment. Sea life, however, offers a potential new advantage. Marine organisms are highly attuned to their surroundings—their survival depends on it—and a new program out of DARPA’s Biological Technologies Office aims to tap into [marine animals] natural sensing capabilities to detect and signal when activities of interest occur in strategic waters such as straits and littoral regions.
The world’s vast oceans and seas offer seemingly endless spaces in which adversaries of the United States can maneuver undetected. The U.S. military deploys networks of manned and unmanned platforms and sensors to monitor adversary activity, but the scale of the task is daunting and hardware alone cannot meet every need in the dynamic marine environment. Sea life, however, offers a potential new advantage. Marine organisms are highly attuned to their surroundings—their survival depends on it—and a new program out of DARPA’s Biological Technologies Office aims to tap into [marine animals] natural sensing capabilities to detect and signal when activities of interest occur in strategic waters such as straits and littoral regions.


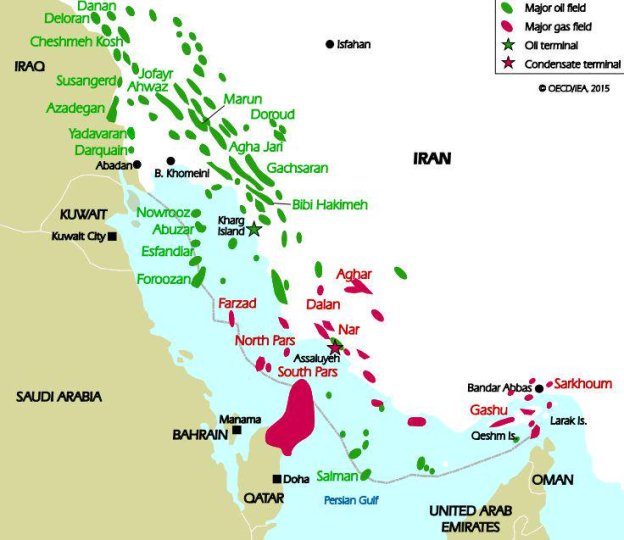
 A withering United Nations report on Yemen’s civil war provides fresh evidence about the extent to which Saudi Arabia and Iran have intervened in the conflict, pursuing their regional proxy war even as Yemen disintegrated into “warring statelets” that would be difficult to reunite. The U.N. panel said there were “strong indications of the supply of arms-related material manufactured in, or emanating from, the Islamic Republic of Iran,” in violation of a U.N. embargo on Yemen.
A withering United Nations report on Yemen’s civil war provides fresh evidence about the extent to which Saudi Arabia and Iran have intervened in the conflict, pursuing their regional proxy war even as Yemen disintegrated into “warring statelets” that would be difficult to reunite. The U.N. panel said there were “strong indications of the supply of arms-related material manufactured in, or emanating from, the Islamic Republic of Iran,” in violation of a U.N. embargo on Yemen.


 As the overthrow of despot Robert Mugabe entered a stalemate on November 17, 2017, eyes turned to China — Zimbabwe’s largest foreign investor and a key ally — amid speculation over its role in the military coup.Source in Harare believe the Zimbabwean conflict within the ruling party Zanu PF is involving two rival camps has direct links to China and Russia with both countries trying to control and protect their own economic interests.
As the overthrow of despot Robert Mugabe entered a stalemate on November 17, 2017, eyes turned to China — Zimbabwe’s largest foreign investor and a key ally — amid speculation over its role in the military coup.Source in Harare believe the Zimbabwean conflict within the ruling party Zanu PF is involving two rival camps has direct links to China and Russia with both countries trying to control and protect their own economic interests.










 On June 22nd 2017,
On June 22nd 2017, 



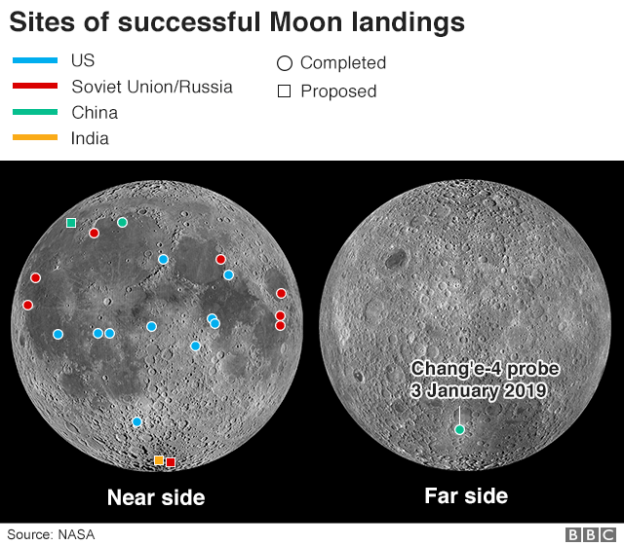
 A SpaceX Falcon rocket lifted off from the Kennedy Space Center in Florida on May , 2017 to boost a classified spy satellite into orbit for the U.S. military, then turned around and touched down at a nearby landing pad.
A SpaceX Falcon rocket lifted off from the Kennedy Space Center in Florida on May , 2017 to boost a classified spy satellite into orbit for the U.S. military, then turned around and touched down at a nearby landing pad.